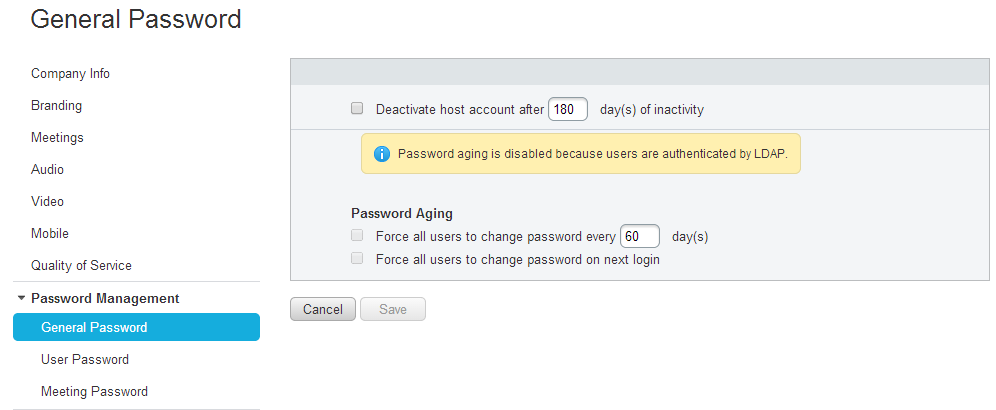
If your organization uses Cisco WebEx Meetings Server with AD directory and AD authentication and you have configured the Directory Integration according to the CWMS Administration Guide, you may be due for a surprise within a few months of initial configuration with a number of users being turned inactive. “But why?!” you ask. Remember that setting about password aging that supposedly does not apply to AD authenticated users? I’m talking about this one:
Well, turns out that if initially synchronized users did not login to CWMS within the default 180 days, their accounts get deactivated. Naturally, one would want to re-activate the accounts and, if you are dealing with a large number of users, you would almost always choose to activate in bulk using CSV file. A word of caution here: activating a large number of users with CSV import also triggers AD Activation Email to be sent out to all enabled users (even if the option to automatically notify users is unchecked under Users -> Directory Integration:
You may want to modify the AD Activation Email template (found under Settings -> Email -> Templates) or, if you prefer WebEx Meetings Server not to reach out to end users, configure a Hub Transport rule on your Exchange server to automatically discard or redirect messages with “Action Required: Activate account” in the Subject line. Which is precisely what I have done:
[PS] C:>New-TransportRule -Name "Disable CWMS AD Activation Email" -SubjectOrBodyContainsWords "Action Required: Activate account" -FromAddressContainsWords "cwms.ucpro.ca" -Comments "This rule disables AD Activation email from Cisco WebEx Meetings Server" -Enabled $true Name State Priority Comments ---- ----- -------- -------- Disable CWMS AD Activation Email Enabled 10 This rule disables AD Activation email from Cis...
I am not sure if disabling the password aging policy would prevent the active accounts from going inactive after 180 days (or some other value if different from default), but I recommend disabling the supposedly inapplicable password aging policy anyway.